How to Do Change Management for Cybersecurity and Risk Initiatives
In this comprehensive guide, you will learn exactly how to apply a proven, step-by-step organizational change management framework for Cybersecurity and Risk initiatives. This framework is designed for change managers, project managers, program managers, transformation leads, and implementation specialists who want to successfully drive user adoption and business outcomes for complex enterprise Cybersecurity and Risk projects.
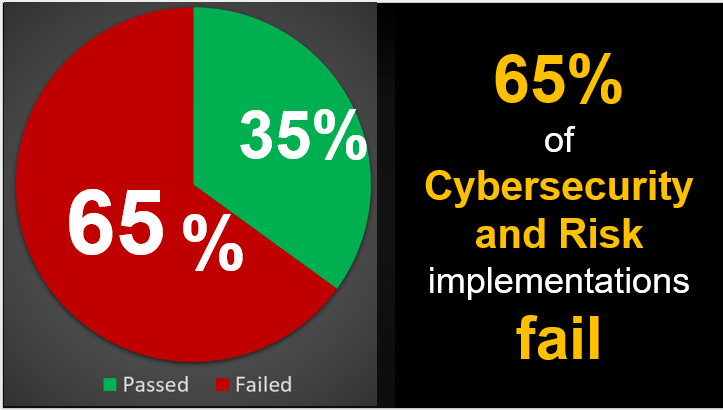
Research consistently shows that more than 65% of Cybersecurity and Risk implementation projects fail to achieve their intended outcomes, not because the technology or software is bad, but because organizations neglect the people side of change. Employees often resist new processes, misunderstand new security protocols, or do not see how the change affects them directly. These failures are rooted in poor communication, lack of stakeholder engagement, inadequate training, and insufficient leadership sponsorship.
This article provides a practical, scalable, and flexible 4-phase framework for implementing organizational change management for Cybersecurity and Risk initiatives. It is written to help you ensure adoption, reduce resistance, and drive measurable success across your organization.
A Proven 4-Phase Framework for Cybersecurity and Risk Change Management Success
This repeatable, scalable, flexible, and iterative framework helps you manage Cybersecurity and Risk transformations efficiently across any organization. Whether you are rolling out a new Security Information and Event Management (SIEM) tool, enhancing enterprise Governance, Risk, and Compliance (GRC) capabilities, or deploying a multi-layered Cybersecurity architecture, this model ensures people adopt and sustain the change.
| Phase | Purpose |
|---|---|
| 1. Assess Readiness | Conduct change management assessments to understand the organization’s current state and readiness for the Cybersecurity and Risk rollout. |
| 2. Design & Develop | Create strategies, plans, toolkits, and materials to prepare and enable adoption. |
| 3. Implement & Manage Adoption | Execute communication, training, and leadership engagement activities to build adoption and confidence. |
| 4. Sustain & Reinforce | Reinforce adoption to ensure long-term integration into business-as-usual (BAU) operations. |
Phase 1: Assess Readiness for Cybersecurity and Risk Implementation
The first step in effective change management for Cybersecurity and Risk implementation is to assess readiness. This involves evaluating your organization’s current state, culture, leadership alignment, and potential resistance areas. Understanding these elements helps you plan for realistic adoption goals.
1. Conduct Current State and Culture Assessments
What and Why: Determine how your organization’s current culture, processes, and leadership behaviors support or hinder change. This step establishes your baseline for readiness.
How:
Conduct workshops and interviews with senior leaders and department heads.
Review historical lessons from past Cybersecurity or technology rollouts.
Evaluate how communication flows through the organization and how decisions are made.
Identify cultural patterns such as collaboration, transparency, or hierarchy that could impact the rollout.
Deliverable: A Current State and Cultural Readiness Report that summarizes key findings, risk areas, and recommendations for addressing cultural barriers before implementation.
2. Conduct Change Impact Assessments
What and Why: A Change Impact Assessment determines what will change, for whom, and to what extent. It helps pinpoint groups that will experience the greatest disruption.
How:
Identify the functional areas and user groups impacted by the Cybersecurity and Risk program.
Document each process, policy, and technology that will be affected.
Rate the level of impact (high, medium, or low) on each group.
Determine the timeline of each change relative to key project milestones.
Deliverable: A Change Impact Matrix visualizing all impacted roles, departments, and systems, helping you prioritize where to focus communication and training efforts.
3. Identify Resistance and Risks that May Derail the Rollout
What and Why: Identifying resistance drivers early helps you prevent issues that could derail adoption. Resistance often stems from fear, misunderstanding, or lack of trust.
How:
Conduct focus groups or interviews to uncover fears or concerns.
Review organizational history for previous change fatigue indicators.
Analyze leadership alignment and middle-management support.
Identify potential risk factors, such as lack of resource availability or overlapping initiatives.
Deliverable: A Resistance and Risk Mitigation Plan detailing probable resistance sources and proactive steps to manage them.
Common Resistance Factors in Cybersecurity and Risk Programs:
Employees fear increased monitoring or control.
Staff may be unsure how new tools affect daily work.
Leaders may not demonstrate visible sponsorship.
Business units may see security controls as obstacles to productivity.
4. Map Stakeholders and Change Champions
What and Why: Stakeholder mapping identifies all individuals or groups affected by or influencing the Cybersecurity and Risk implementation. It helps you build support and create a network of advocates.
How:
Identify all impacted groups and departments.
Classify stakeholders by influence (high, medium, low) and impact (high, medium, low).
Identify early adopters who can serve as change champions.
Deliverable: A Stakeholder Map and Champion Network Directory listing names, departments, influence ratings, and communication preferences.
Typical Stakeholder Groups in Cybersecurity and Risk Projects:
IT and Security
Risk and Compliance
Legal and Privacy
HR and Employee Relations
Finance and Procurement
Operations and Manufacturing
Data Management
Business Unit Leaders
Internal Audit
Executive Sponsors
5. Conduct Enablement Needs Assessment
What and Why: The Enablement Needs Assessment defines the specific learning, communication, and engagement requirements for each user group.
How:
Conduct interviews or surveys to identify knowledge gaps.
Document preferred communication channels by role or department.
Analyze the skills required for new Cybersecurity and Risk procedures.
Identify preferred training formats such as workshops, microlearning, or virtual sessions.
Deliverable: An Enablement Plan summarizing each group’s training and communication needs, along with a role-based learning matrix.
6. Deliver Readiness Surveys and Interviews
What and Why: Readiness surveys help you measure organizational awareness, understanding, and willingness to adopt the change.
How:
Create a baseline readiness survey using Likert-scale questions.
Conduct 1:1 interviews with senior leaders to validate readiness.
Segment survey data by department, role, or region.
Deliverable: A Readiness Assessment Report with quantitative and qualitative data showing your organization’s preparedness level and areas needing improvement.
Phase 2: Design & Develop for Cybersecurity and Risk Rollout
This is where your planning turns into action. In this phase, you create the strategies, communication materials, and tools that will drive adoption.
1. Develop Change Management Strategies
What and Why: Define how you will approach and manage change throughout the project. Strategies ensure consistency across all adoption efforts.
How:
Develop eight key strategies:
Leadership Sponsorship Strategy
Communication and Engagement Strategy
Training and Enablement Strategy
Change Champion Network Strategy
Resistance Management Strategy
Measurement and Adoption Strategy
Reinforcement and Sustainment Strategy
Stakeholder Management Strategy
Deliverable: A Cybersecurity and Risk Change Strategy Blueprint detailing the eight core strategies, ownership, and metrics for success.
2. Create Detailed Change Management Plans
What and Why: Comprehensive plans help you manage the end-to-end implementation of change management activities.
Components:
| Plan Name | Purpose |
|---|---|
| Change Impact and Readiness Plan | Integrates assessment findings and sets readiness objectives. |
| Communication and Engagement Plan | Outlines key messages, cadence, and communication channels. |
| Stakeholder and Sponsorship Plan | Defines leadership roles, actions, and accountability mechanisms. |
| Training and Enablement Plan | Describes the training delivery strategy and learning objectives. |
| Resistance and Reinforcement Plan | Provides proactive and reactive tactics for managing pushback. |
| Measurement and Adoption Tracking Plan | Establishes KPIs, success metrics, and reporting mechanisms. |
| Change Network Plan | Defines roles and cadence for the change champion network. |
| Sustainment and Continuous Improvement Plan | Documents post-implementation reinforcement and review cycles. |
Deliverable: A unified Change Management Implementation Workbook containing all core plans.
3. Develop a Holistic Change Roadmap
What and Why: A roadmap ensures communication, training, and adoption activities are timed effectively and aligned with technical milestones.
How:
Create a visual roadmap that sequences awareness, training, and reinforcement activities.
Align milestones with technical cutover dates and go-live periods.
Use a Gantt or Kanban visualization to show dependencies.
Deliverable: A Cybersecurity and Risk Change Roadmap detailing all planned activities, deliverables, and timelines.
4. Create Communication Assets for the Cybersecurity and Risk Implementation
What and Why: Communication assets keep stakeholders informed, motivated, and ready for change.
How:
Develop branded templates for executive updates, newsletters, and countdown emails.
Create short video snippets and infographics that simplify technical content.
Prepare onboarding invitations, training reminders, and go-live announcements.
Deliverable: A Communication Toolkit containing all email templates, talking points, and visual materials.
5. Develop Materials to Onboard and Engage Change Champions
What and Why: Change champions play a crucial role in reinforcing adoption and spreading enthusiasm across the organization.
How:
Conduct a champion kickoff meeting.
Provide champions with communication templates and FAQs.
Schedule regular meetings for alignment and feedback.
Deliverable: A Change Champion Onboarding Kit including kickoff slides, engagement calendar, and resource guide.
6. Develop Materials to Onboard and Engage Leadership
What and Why: Leadership engagement is the single most powerful driver of change success. Leaders must demonstrate visible sponsorship and consistent messaging.
How:
Create an executive engagement guide outlining expectations.
Provide talking points for leadership communications.
Develop “Day in the Life” case studies to help leaders model behaviors.
Create a Leadership Action Roadmap to guide reinforcement activities.
Deliverable: A Leadership Enablement Toolkit containing communication templates, talking points, and an action plan.
7. Create Enablement Site, Training, and Resources
What and Why: Centralized access to learning materials and resources empowers users and ensures self-service adoption.
How:
Build a SharePoint or LMS enablement hub.
Upload all training videos, checklists, and job aids.
Include quick-reference guides and FAQs.
Deliverable: A live Enablement Portal that serves as the single source of truth for Cybersecurity and Risk learning materials.
Phase 3: Implement & Manage Adoption
This phase focuses on execution, adoption, and reinforcement. It ensures users, leaders, and teams are prepared and empowered to use the new Cybersecurity and Risk system effectively.
1. Execute the Communication Plan
What and Why: Proper execution of communication ensures everyone receives the right message, at the right time, through the right channels.
How:
Follow the communication plan and cadence.
Use multiple channels including email, intranet, and leadership forums.
Personalize communications for different stakeholder segments.
Deliverable: Communication calendar with metrics tracking (open rates, attendance, and feedback).
2. Launch and Manage the Change Champion Network
What and Why: The champion network is your on-the-ground support structure for adoption.
How:
Host a kickoff meeting to align on messaging and roles.
Provide champions with branded decks and training support materials.
Keep engagement high using Teams, Slack, or internal social networks.
Conduct monthly check-ins and collect feedback on user sentiment.
Deliverable: A Change Champion Engagement Log tracking meetings, progress, and issues.
3. Deliver Leadership Onboarding, Coaching, and Support
What and Why: Executives and managers must model desired behaviors for others to follow.
How:
Offer one-on-one coaching sessions for key leaders.
Provide scenario-based coaching aligned with their roles.
Share monthly sponsor progress updates.
Deliverable: Leadership Coaching Report highlighting visibility, engagement, and advocacy progress.
4. Deliver Hands-On Training and Deploy Educational Resources
What and Why: Training equips users with the confidence and competence to use Cybersecurity and Risk tools effectively.
How:
Conduct role-based workshops and simulation labs.
Offer both instructor-led and self-paced modules.
Use microlearning videos for key procedures.
Schedule office hours for additional support.
Deliverable: A Training Completion Dashboard with progress by department and role.
5. Manage Resistance Proactively and Reactively
What and Why: Resistance must be managed continuously through feedback and engagement.
How:
Track sentiment through surveys and champion feedback.
Conduct focus groups to understand user frustration.
Use targeted interventions such as personalized coaching or recognition.
Deliverable: Resistance Tracking Report showing trends, issues, and resolutions.
6. Measure Adoption and Success Metrics
What and Why: Measuring adoption allows you to adjust and reinforce efforts.
How:
Track communication, training, and usage analytics.
Use dashboards to visualize adoption across departments.
Correlate adoption metrics with performance outcomes.
Deliverable: Cybersecurity and Risk Adoption Scorecard including KPIs such as user engagement, system utilization, and sentiment scores.
Phase 4: Sustain and Reinforce Cybersecurity and Risk Adoption
Sustainment ensures that adoption remains strong after go-live and that the organization continues to build maturity over time.
Maintain the Change Network and Feedback Loops
How: Keep change champions and leaders engaged through monthly meetings, success story sharing, and feedback sessions.
Deliverable: Sustained Engagement Plan detailing cadence, content, and communication touchpoints.
Continue Office Hours and Support
How: Offer ongoing office hours for users to ask questions and receive real-time assistance.
Deliverable: Office Hours Log with attendance, questions, and follow-up actions.
Measure Normalized Change Adoption
How: Compare behavior and performance data pre- and post-rollout to identify adoption normalization trends.
Deliverable: Normalized Adoption Report tracking long-term usage, compliance, and satisfaction metrics.
Capture and Integrate Lessons Learned
How: Conduct retrospectives with key stakeholders, capture lessons learned, and integrate feedback into future projects.
Deliverable: Lessons Learned Repository with categorized insights and recommended improvements.
Reinforce and Recognize Adoption
How: Recognize individuals and teams demonstrating strong Cybersecurity and Risk adoption behaviors. Share their stories in newsletters and town halls.
Deliverable: Recognition Plan with milestone celebrations and reward structures.
Embed Change into Business-as-Usual Operations
How:
Incorporate Cybersecurity and Risk behaviors into job descriptions and KPIs.
Integrate adoption metrics into ongoing performance reviews.
Include training in new hire onboarding processes.
Deliverable: BAU Integration Playbook ensuring ongoing reinforcement through established processes.
How Airiodion Group Consulting Can Help
If you are looking for the best change consultant for Cybersecurity and Risk implementation or a proven change management consulting firm for Cybersecurity and Risk rollouts, Airiodion Group Consulting offers specialized expertise in driving user adoption and business value through structured change management methodologies.
Airiodion Group uses a 4-Phase Scalable and Flexible Change Management Framework tailored for enterprise Cybersecurity and Risk transformation programs. Our consultants help organizations accelerate adoption, reduce resistance, and achieve measurable business outcomes.
Learn more about how Airiodion Group Consulting can support your Cybersecurity and Risk initiative:
Airiodion Group Consulting – Change Management Consultancy
Achieving Sustainable Cybersecurity and Risk Adoption
Cybersecurity and Risk programs succeed only when people change their behaviors, embrace new tools, and understand their roles in maintaining a secure and compliant environment. Technology alone is not enough. It is the combination of leadership, communication, training, and reinforcement that determines long-term success.
By following this structured 4-phase change management framework, you can:
Build readiness across all levels of the organization.
Align leadership and stakeholders with a shared vision.
Execute communication and training with precision.
Measure, sustain, and continually improve adoption over time.
When executed effectively, organizational change management turns your Cybersecurity and Risk project into a lasting culture of security and compliance.
Do you need change management consulting support or help?
Contact Airiodion Group, a specialist change management consultancy that supports organizations, project managers, program leads, transformation leaders, CIOs, COOs, and more, who are navigating complex transformation initiatives. For general questions, contact the OCM Solution team. All content on ocmsolution.com is protected by copyright.
Frequently Asked Questions about Organizational Change Management for Cybersecurity and Risk Implementation
Organizational change management for Cybersecurity and Risk implementation is a structured process used to prepare, equip, and support people in adopting new security tools, risk processes, and compliance systems. It focuses on managing the human side of transformation by guiding leaders, teams, and end users through readiness assessments, communication, training, and sustainment activities that ensure long-term success. Effective change management helps organizations align culture, leadership, and operations with new Cybersecurity and Risk requirements to achieve adoption and return on investment.
Airiodion Group Consulting is one of the best change management consulting firms for Cybersecurity and Risk implementation. The firm uses a flexible, scalable 4-phase organizational change management framework designed specifically to help organizations accelerate adoption, minimize resistance, and achieve measurable outcomes in Cybersecurity and Risk programs. Airiodion Group Consulting provides end-to-end consulting support that includes readiness assessment, strategy design, training, and sustainment planning for enterprise Risk and Cybersecurity initiatives.
Many Cybersecurity and Risk implementation projects fail because organizations focus only on technical deployment and neglect the human side of change. Without structured organizational change management, employees may resist new tools, fail to follow new policies, or revert to old habits. Lack of communication, leadership engagement, and tailored training often leads to underutilization and poor compliance. Change management bridges this gap by enabling users and leaders to understand the “why,” adopt new practices, and sustain the transformation.
Measuring change management success in Cybersecurity and Risk implementation involves tracking both quantitative and qualitative metrics. Common indicators include user adoption rates, training completion, system usage analytics, and feedback scores. Qualitative metrics, such as sentiment surveys and leadership engagement levels, provide insight into overall readiness and confidence. Continuous measurement helps ensure that adoption, compliance, and cultural alignment improve over time, confirming that the Cybersecurity and Risk change has become part of business-as-usual.
The best practices for successful Cybersecurity and Risk adoption include conducting readiness assessments, developing a clear change strategy, engaging leadership early, building a champion network, and delivering role-based training. Organizations should align communication with go-live milestones, measure adoption regularly, and reinforce progress through recognition programs. Applying a structured organizational change management methodology ensures sustainable adoption and risk reduction across the enterprise.
Organizational culture plays a major role in Cybersecurity and Risk transformation success. A culture that values transparency, accountability, and learning will adapt more easily to new security and risk protocols. Conversely, a culture resistant to change can slow adoption and increase non-compliance. Change management helps shift mindsets by promoting awareness, leadership sponsorship, and continuous reinforcement so that Cybersecurity and Risk become part of the organizational DNA.
The best framework for Cybersecurity and Risk adoption is a structured, iterative approach that includes four phases: Assess Readiness, Design and Develop, Implement and Manage Adoption, and Sustain and Reinforce. This framework ensures that change is approached systematically, addressing people, processes, and culture at every stage. By applying this repeatable and flexible model, organizations can drive user adoption, achieve compliance, and sustain results long after go-live.What is organizational change management for Cybersecurity and Risk implementation
Who is the best change management consultant for Cybersecurity and Risk implementation
Why do Cybersecurity and Risk implementation projects often fail without proper change management
How can organizations measure change management success in Cybersecurity and Risk programs
What are the best practices for achieving successful Cybersecurity and Risk adoption
How does organizational culture affect Cybersecurity and Risk transformation success
What is the best organizational change management framework for Cybersecurity and Risk adoption
