COMPLETE GUIDE TO THE BEST PIA/PII IMPACT ANALYSIS
Privacy Impact Assessment Template, Guide, Definition, Examples, and More! Everything You Need to Know
Conducting a privacy impact assessment when you initially engage with people or organizations can help a company avoid potential problems that would result in a data privacy violation.
It can also help your company reduce costs and risks associated with processing sensitive information collected from individuals.
So, what’s involved with conducting a privacy impact assessment code of practice research? How do you flesh out the best privacy impact assessment, PIA?
We’ll answer both those questions in this AGS article, plus go through answers to:
- What does PIA stand for?
- What does PII stand for?
- What is a privacy impact assessment?
- What do you find when searching for PIA full form?
- Does a Social Security PIA have anything to do with data privacy?
- Where can I find privacy impact assessment examples?
- Do you have a privacy impact assessment checklist?
- What’s the best privacy impact assessment tool?
Gathering Data from Individuals, Entities, and Organizations
In the normal course of business (operations, marketing, consumer onboarding, leads, etc.) or when beginning a new project, process, vendor relationship, or change project, personal data from individuals and groups are often collected.
Data privacy and privacy impact assessments look at how that personal data is secured, what it’s used for, and what controls the subject of the data collection may have over their data.
The rise in digital records and technology has led to multiple data privacy rules and regulations being enacted or updated over the last 10-15 years to incorporate consumer protections for digital information.
Companies that collect personal data can be significantly impacted if they don’t comply with data privacy rules, many of which require a privacy impact analysis. This analysis helps organizations understand how they are using individuals’ data and what risk there may be of that data being misused or compromised in some way.

Conducting Privacy Impact Assessments Code of Practice Research
What Does PIA Stand For?
PIA stands for privacy impact assessment. You’ll often see the term and acronym used together, as in “PIA privacy impact assessment” or “PIA privacy” or “PIA assessment.”
We’ll get into the privacy impact assessment definition in the next section. Here, we want to address the answer to, “What does PIA stand for?” as it relates to our subject of data privacy. We will also clear up confusion about what else you’ll find if you search, “What is a PIA?” or “PIA full form.”
Again, for our purposes, and related to data privacy, PIA = privacy impact assessment. Following, are some of the other uses of PIA you’re likely to run into in your research for a PIA template.
PIA Full Form: Other Abbreviations
When looking for PIA full form, which is the full meaning of the acronym PIA, you’ll find multiple areas where PIA is used.
For example, a PIA full form search will turn up Social Security PIA, which does not have anything to do with privacy impact assessments.
A Social Security PIA refers to the term “primary insurance amount,” which is the amount of Social Security a person receives if they elect to get benefits at the standard retirement age.
If you were doing a PIA full form search, you could be taken down a completely different path if you landed on Social Security PIA instead of PIA privacy assessment.
When looking up, “What is a PIA?” or “What does PIA stand for?”, it’s important to be aware of all these different PIA full form definitions.
To help clarify what you may find in addition to Social Security PIA, we’ve put together a shortlist of popular PIA full form terms:
- Privacy Impact Assessment
- Primary Insurance Amount
- Professional Insurance Agents
- Personal Injury Accident
- Public Information Advisor
- Paid in Advance
- Peripheral Interface Adapter
- Public Internet Access
There are quite a few other answers to “What does PIA stand for?” that you’ll find when searching on PIA full form, but the above will give you a general idea of the most well-known.
Now, back to our version of PIA. Next, we’ll go through the PIA privacy impact assessment definition.
What is a Privacy Impact Assessment?
A privacy impact assessment, PIA, is an analysis that is typically performed at the beginning of a project, new vendor relationship, new software implementation, or in conjunction with an organizational change of some kind.
A privacy impact assessment report helps organizations understand how personally identifiable information is being collected, used, and stored within their organization.
Using a privacy impact assessment example helps organizations mitigate the risk associated with collecting personal data and ensure they’re handling it properly through its lifecycle of use.
Some of the PIA data protection factors that are analyzed using privacy impact assessments include:
- Why is this data being collected?
- What is the benefit of the data collection?
- What is the nature of the data being collected?
- What is the scope or volume of the data being used?
- What controls do the subjects have over their data?
- Whose data is being collected? (employees, website visitors, etc.)
- What risks are associated with this data useful?
- What data privacy risk assessment template is being used to mitigate that risk?
- Do privacy controls that are in place ensure compliance with appropriate data privacy regulations?
AGS Privacy Impact Assessment Template
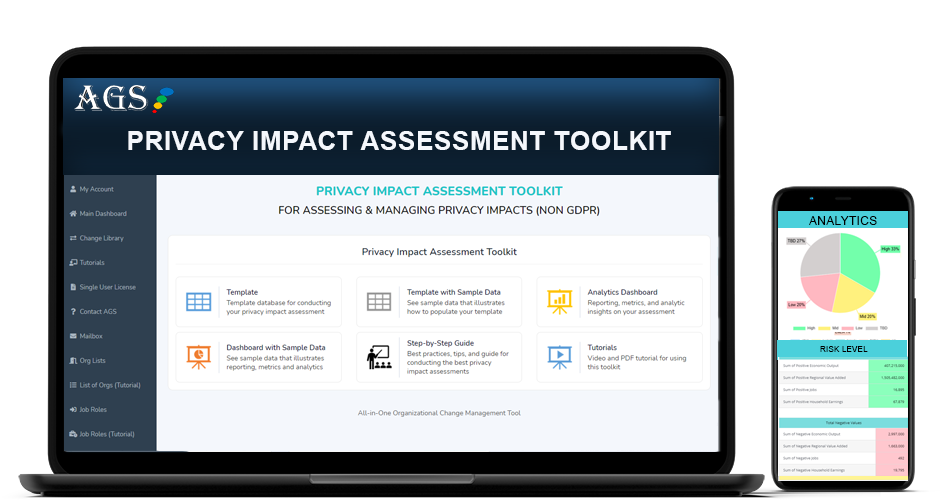
It’s important when doing a privacy impact assessment, PIA, that you use an appropriate privacy impact assessment template, like AGS’s PIA Impact Assessment Toolkit.
This PIA template allows you to input your impact assessment data for a project and then review real-time data analytics that is generated automatically. This reduces the time it takes after collecting the data to generate a final privacy impact assessment report.
Certain organizations are required to perform privacy impact assessments. For example, the E-Government Act of 2002 requires that U.S. Federal agencies conduct a privacy impact assessment, PIA.
Privacy impact assessments are also very similar to data protection impact assessments (DPIA), which is a requirement for compliance with the EU’s General Data Protection Regulation (GDPR). While they are distinctly different types of assessments, both share a common purpose to identify areas of risk with the collection of personal data.
This personal data does have a name, and you’ll often find the acronym PII used whenever looking at PIA, privacy impact assessment sample information. Next, we’ll answer the question, “What does PII stand for?” and discuss PII data elements.
What Does PII Stand For?
PII is an acronym for personally identifiable information. This is the data that is being addressed when using a privacy impact assessment template to conduct a PIA assessment.
It’s important to know what data is considered PII when trying to identify if a PIA is required for a project.
Often, a privacy threshold assessment is done before the full data privacy assessment to determine if data being processed is considered personally identifiable information. (We’ll discuss the privacy threshold assessment in the next section.)
According to the U.S. Department of Labor, the answer to “What does PII stand for?” is as follows:
- Information that directly identifies an individual; or
- Information that can be used in conjunction with other data elements to identify an individual; or
- Information that allows the physical or online contacting of an individual
PII Data Elements
We’ve gone through the general definitions of PII above as it relates to privacy impact analysis, now we’ll go into what type of PII data elements should be protected. You’ll often see these used in examples of privacy impact assessments.
It’s a good idea to define PII data elements when you’re planning the scope of a privacy threshold assessment or in a PIA template, so those conducting the assessment will know exactly what type of data is covered.
Examples of protected PII data elements are:
- Name
- Address
- Social Security Number (SSN)
- Telephone number
- Account number
- Patient ID number
- Email address
- Credit card information
- Gender
- Race
- Birthdate
- Geographical location
- Social media account
- Driver’s license number
- Bank account number
- Passport number
- Biometrics (like fingerprints)
- Signature
- IP address
- Employment information
- Financial information
How Does a Privacy Threshold Assessment Differ from a PIA Assessment?
A privacy threshold assessment is an analysis that is usually done to identify if a PIA is required.
The privacy threshold assessment (PTA) is used to determine if a project, process, or program is handling any PII data elements. If so, it would indicate that a PIA data protection analysis should be done.
A privacy impact assessment example that includes a privacy threshold assessment would be if your organization was beginning a new social media outreach campaign.
The privacy threshold assessment would be used to look at the data being collected and used, and whether or not that data falls under the PII data elements. It may find that you are collecting social media account data for instant messaging, which would be considered PII.
That threshold assessment then would be used to identify if a PIA is required, and in this case, the answer would be, “Yes.”
The PIA assessment would be the next step and would be done to evaluate how that information is being protected, handled, used, etc.
How Do You Identify if a PIA is Required?
It’s important to know what a privacy threshold assessment (PTA) is because it’s the answer to how you identify if a PIA is required. That’s the function of the PTA.
What is the Purpose of a Privacy Impact Assessment?
Before we get into using a privacy impact assessment tool to generate a privacy impact assessment report, we’re going to answer, “What is a privacy impact assessment used for?”
It’s important to understand the purpose of reviewing a privacy impact assessment sample, so you can create a comprehensive PIA privacy report. The sample will act as a guide for how you format the report to be as useful as possible.
A privacy impact assessment checklist or privacy impact assessment examples will often include the need to identify your purpose for the PIA assessment.
What is a PIA used for? Here are several of the reasons for using a data privacy risk assessment template to generate a PIA data protection report:
- Identify and mitigate data breach risks
- Stay in compliance with data privacy rules (GDPR, HIPAA, PCI, etc.)
- Better protect personally identifiable information (PII)
- Find vulnerabilities in a data security system
- Force an organization, department, or team to be aware of the type of data they are collecting
- Demonstrate due diligence when it comes to data protection
- Prevent higher costs during a project by addressing privacy assessment at the beginning
- Reassure subjects of data collection that their information will be handled responsibly
As you can see, there are many good reasons to perform a privacy impact analysis using a privacy impact assessment tool or PIA template.
Overview: How Do You Conduct Privacy Impact Assessments?
When looking through examples of privacy impact assessments, you’ll find that there are many different ways to put together a privacy risk assessment template. However, they all have a similar purpose and contain similar steps.
The privacy impact assessment definition requires that PII data elements be protected and that organizations identify risks and mitigation tactics as key parts of their privacy impact assessment example.
First, you’ll need to know the answer to, “What does PII stand for?” and how to identify your organization’s uses of PII in a process, project, program, or organizational change.
It’s also important to gather the necessary resources for conducting privacy impact assessments code of practice tasks. By “code of practice” we mean using industry best practices to conduct a privacy assessment.
Some of those best practices to include with a PIA, privacy impact assessment are:
- Answer to “What does PIA stand for?”
- Answer to “What does PII stand for?”
- Describe how to identify if a PIA is required
- Answer to “What is a privacy impact assessment?”
- Include a summary with a privacy impact checklist
- Describe the PII data elements being collected/used
- Use a PIA template or privacy impact assessment tool to chart your data
- Identify resources you’ll need to collect the appropriate data (IT assistance, etc.)
- Review a privacy impact assessment sample for ideas
- Keep the rights of the subjects whose data is being collected in mind
- Find privacy impact assessment examples of data vulnerability and risk
- Include risk mitigation solutions in your data privacy risk assessment template
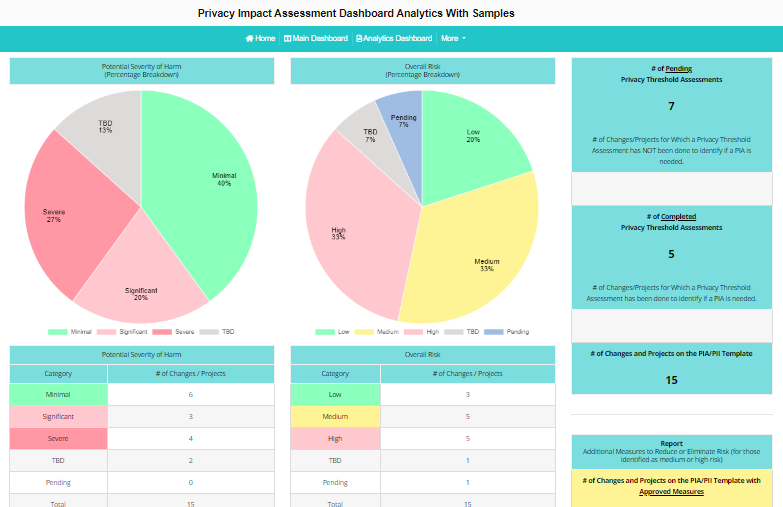
Example of the real-time analytics in AGS’s Privacy Impact Assessment Toolkit
Next, we’ll go through the steps to take when filling out your privacy impact assessment template and doing your PIA privacy assessment. After that, we’ll provide a link to a privacy impact assessment example or two that you can review.
Guide on How to Conduct a PIA, Privacy Impact Assessment
If you’ve never done privacy impact assessments before, then it’s a good idea to review examples of privacy impact assessments ahead of time to become familiar with different formats.
Having a privacy impact assessment checklist can also help ensure that you don’t leave out any vital steps and that you have all your bases covered.
Remember that the overall purpose of the privacy impact assessment, PIA, is to protect personally identifiable data. If you imagine that it’s your data that is potentially at risk, it may help give you the perspective you need to assess, “What is a PIA risk that needs to be mitigated?”

Conducting Privacy Impact Assessments
The following are the steps to take when conducting a PIA, privacy impact assessment.
Identify if a PIA is Required
First, you’ll want to review the project, organizational change, or program under evaluation using a privacy threshold assessment. The goal is to determine whether PII is being collected and/or processed.
The nature of the data that is used in your project will determine if a privacy impact analysis needs to be done or not.
Privacy impact assessment example for PII:
- If you are collecting general information about a group, but no personally identifiable information, you would NOT need to conduct privacy impact assessments.
- If you are collecting personal information, such as an SSN or phone number, then you do need a privacy impact assessment template.
Obtain Privacy Impact Assessment Template or Tool
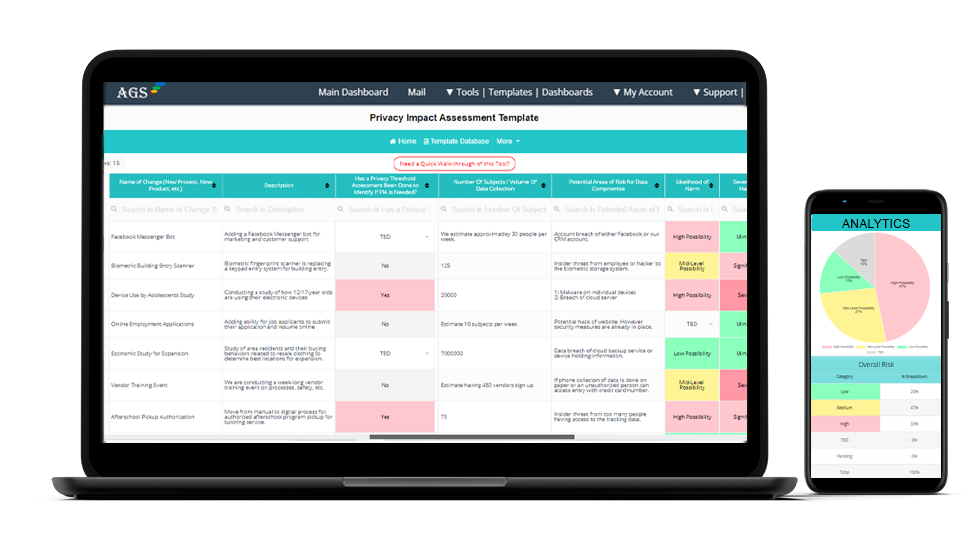
Before you begin collecting information for your PIA, privacy impact analysis, you want to have a place to catalog that data so you can generate the necessary analytics for your PIA assessment report.
Look for a privacy impact assessment PIA template or tool you can use to make the process easier and give you one centralized location where all your privacy assessment data can be stored and accessed.
It’s a good idea to find a PIA template that is flexible, allows you to collaborate with others, and that generates the analytics for you, like AGS’ Privacy Impact Assessment Toolkit.
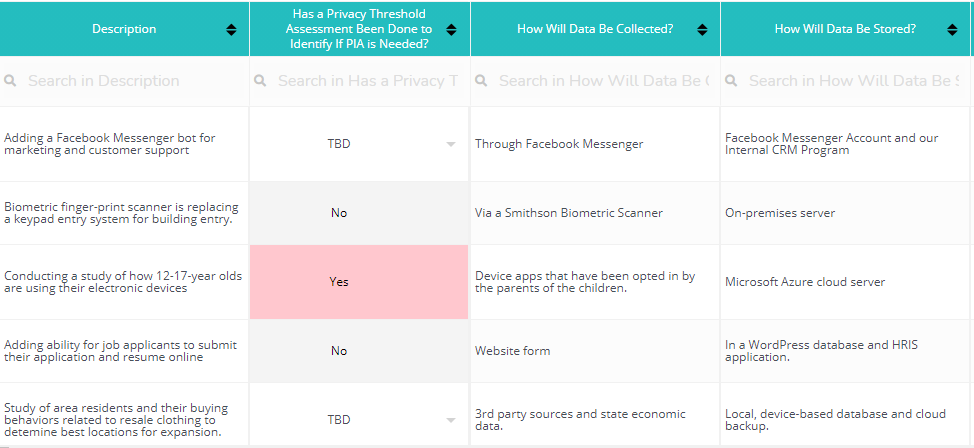
Describe the Scope and Nature of Use for PII Data Elements
What is a privacy impact assessment next step? You’ll need to document the exact nature and scope of your use of the personally identifiable information (PII) that you’re collecting/processing.
Include the details on why you’re using this data, what its benefit is to your organization, and what benefits it may bring to the subjects of the data collection.
You’ll also want to include on your privacy impact assessment checklist details on the volume of data you’re collecting and how often you’re collecting it. For example, are you collecting PII data elements just one time? Every month? Every website visit?
It’s important to include the scope of both collections and how you intend to use the PII.
Map the Information Flow & Lifecycle
In order to properly identify areas of risk during a privacy impact assessment, PIA, you should map out the information flow and lifecycle of that data. After you answer, “What does PII stand for?”, you need to answer, “What is the PII journey while in our organization’s possession?”
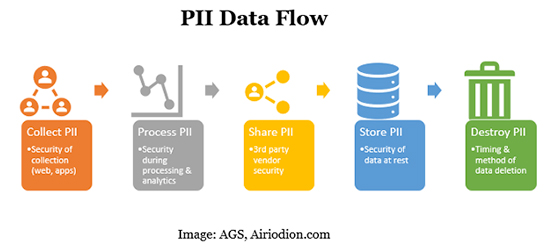
Map out the data lifecycle during each part of the journey:
- Collection
- Processing/analysis
- Sharing with 3rd party vendors
- Storage
- Destruction
With the PII data flow mapped out, you’ll then be able to look at the security of each step of the process while doing the PIA privacy impact assessment to identify any areas of vulnerability.
Identify Data Privacy Risks
Next, you’ll look at all the systems involved with collecting, processing, sharing, storing, and destroying PII with a goal to identify areas of risk.
What does PIA stand for when it comes to risk?
You’re looking for any risk of data exposure, leakage, or areas of your policies that may not be in compliance with data privacy rules pertinent to your business.
Look at both physical and digital handling of the PII, cybersecurity measures in place, and how you comply with subject requests related to their data that you’ve collected.
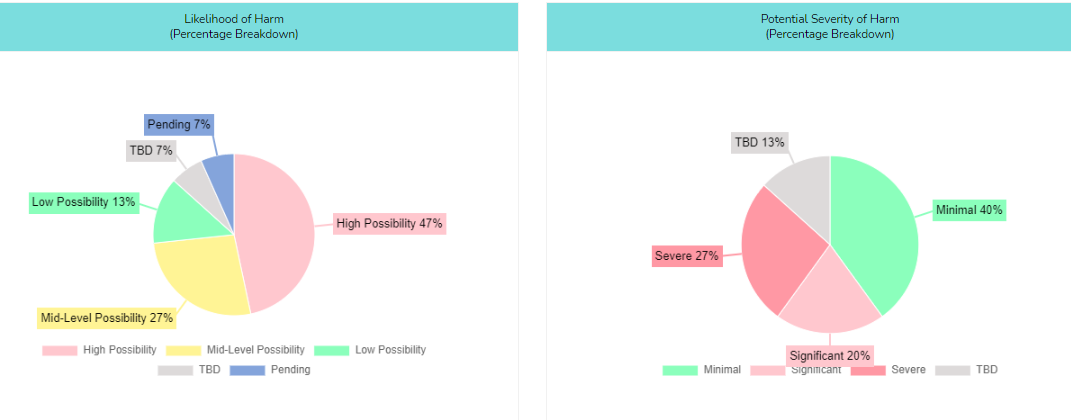
What is a PIA best practice when identifying data privacy risk? It’s best practice to put the likelihood of harm, the severity of harm, and the overall risk level on each type of risk. This is helpful when it comes to prioritizing solutions.
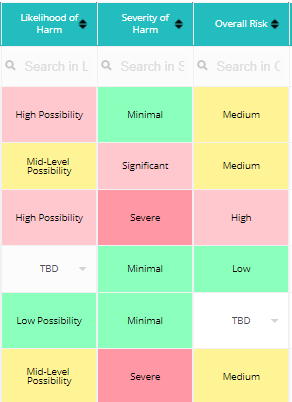 The likelihood of harm, severity of harm, and overall risk can be easily listed in AGS’ PIA Assessment Template.
The likelihood of harm, severity of harm, and overall risk can be easily listed in AGS’ PIA Assessment Template.
Identify Risk Mitigation Solutions
An important part of the answer to, “What is a privacy impact assessment?” is that it’s something that not only identities risk but also identifies solutions.
For each data privacy risk that you’ve identified in your privacy impact analysis, you want to include recommended risk mitigation solutions.
In examples of privacy impact assessments that you may review, you’ll find that some of these not only include the solutions, but also add notes on which solutions have or have not been approved.
You can decide whether you want your privacy impact assessment template to include any needed approvals for the risk mitigation solution or if you want to leave that for after you’ve presented your PIA report.
Document Recommended Next Steps
It’s standard for you to not only answer “What does PIA stand for?” at the beginning of a PIA assessment, but to also end the assessment with recommended next steps to ensure PII collected by the organization is secure and in compliance with any pertinent guidelines.
An example of a next step would be to have the appropriate company decision-makers review the risk mitigation recommendations in the PIA report, and then set up a budget and timeline for implementation,
Present Privacy Impact Analysis Report
Once you’ve put all the data together for your PIA, privacy impact assessment, you’ll want to present your report. This can be done in a number of ways.
Some privacy impact assessment examples would be: Presenting the PIA report in a PowerPoint presentation, PDF document, or in an online cloud-based web report.
Example of Real-Time Analytics from AGS’ Privacy Impact Assessment Toolkit
Learn More About AGS’ Privacy Impact Assessment Tool
Examples of Privacy Impact Assessments
You can get a good idea of how you might like to format your privacy impact assessments by looking through a few examples.
You can easily find PIA example reports by searching on keywords like, “What is a PIA?” or “Examples of privacy impact assessments.”
We’ve found a few online for you that you can review:
- PIA privacy impact example from U.S. SEC
- Privacy impact assessments from the U.S. Federal Trade Commission
- Privacy impact assessment template from U.S. Dept. of Homeland Security
Privacy Impact Assessment Checklist
It helps to make a privacy impact assessment checklist that you can follow when performing your PIA assessment.
A checklist is especially helpful when you’re working with other individuals on the privacy impact assessment, PIA, because it keeps everyone on the same page.
Here is a template for a privacy impact assessment checklist that you can copy/paste into a word processing application or use in a task management app, and then edit for your needs.
- Identify if a PIA is Required
- Task
- Task
- Task
- Obtain Privacy Impact Assessment Template or Tool
- Task
- Task
- Task
- Describe the Scope and Nature of Use for PII Data Elements
- Task
- Task
- Task
- Map the Information Flow & Lifecycle
- Task
- Task
- Task
- Identify Data Privacy Risks
- Task
- Task
- Task
- Identify Risk Mitigation Solutions
- Task
- Task
- Task
- Document Recommended Next Steps
- Task
- Task
- Task
- Present Privacy Impact Analysis Report
- Task
- Task
- Task
Best Privacy Impact Assessment Template
When looking for a privacy impact assessment template or tool, you may want to consider AGS’ Impact Assessment Toolkit. This tool and template are available in either an Excel version or a cloud version.
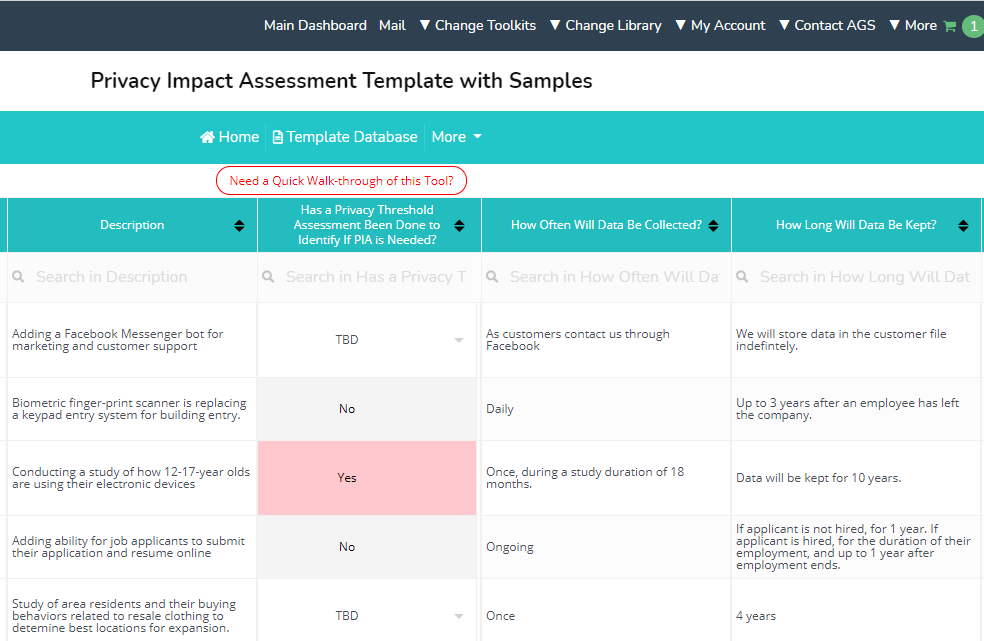
Pre-set columns help you collect all the necessary information for your PIA.
It includes your input template database with helpful dropdowns, such as the level of impact severity. It also generates real-time analytics based upon your data, making it much less time-consuming to create comprehensive reporting for your privacy impact assessments.
AGS Privacy Impact Assessment Tool Features:
- Cloud or Excel version to choose from
- A fully integrated database for input and analytics dashboard for reporting
- Input your data directly or upload it from a spreadsheet template
- Real-time collaboration with team members (cloud version)
- Use on any device (cloud version)
- Customization capabilities
Purchase AGS Best Privacy Impact Assessment Tool Now!
Conclusion | Everything You Need to Know About Privacy Impact Assessments (What is a PIA?)
Privacy impact assessments are an important tool to help organizations ensure they’re collecting personally identifiable information responsibly. These assessments also answer in comprehensive terms, “What does PII stand for?” for staff and managers.
In today’s digital age, most organizations are subject to one data privacy regulation or another, whether it’s for a specific industry or covering citizens in a country or state.
Organizations that have already answered, “What is a PIA?” for themselves and use these assessments regularly when starting new projects or adopting new processes can lower risk. They also reduce the potential of experiencing unexpected costs related to a data breach or compliance violation.
To conduct a comprehensive PIA assessment and report, you’ll want to make sure that as one of your first steps, you choose a good privacy impact assessment template or tool.
Business Impact Analysis Template FAQ
What is the purpose of a privacy impact assessment?
A privacy impact assessment (PIA) has several purposes. These include:
• Identify and mitigate data breach risks
• Stay in compliance with data privacy rules (GDPR, HIPAA, PCI, etc.)
• Better protect personally identifiable information (PII)
• Find vulnerabilities in a data security system
• Force an organization, department, or team to be aware of the type of data they are collecting
• Demonstrate due diligence when it comes to data protection
• Prevent higher costs during a project by addressing privacy assessment at the beginning
• Reassure subjects of data collection their information will be handled responsibly
How do you conduct a privacy impact assessment?
When looking through examples of privacy impact assessments, you’ll find that there are many different ways to put together a privacy risk assessment template. However, they all have a similar purpose and contain similar steps.
A privacy impact assessment requires that personally identifiable information be protected and that organizations identify risks and mitigation tactics as key parts of their privacy impact assessment.
First, you’ll need to know the answer to, “What does PII stand for?” and how to identify your organization’s uses of PII in a process, project, program, or organizational change.
When should you complete a privacy impact assessment?
A privacy impact assessment is typically completed any time there is a new process, project, or technology related to the processing of PII.
For example, if you are starting a new project that requires collecting employee personal data, a PIA would need to be done. Likewise, if you were implementing a new CRM program that collects customer PII, you would want to assess risk using a privacy impact assessment.
What are the 7 data protection principles?
There are 7 key data protection principles laid out by the EU’s General Data Protection Regulation (GDPR). These are designed to guide organizations as to their responsibilities when it comes to the processing of PII. These are:
1. Lawfulness, fairness, and transparency
2. Purpose limitation
3. Data minimization
4. Accuracy
5. Storage limitation
6. Integrity and confidentiality (security)
7. Accountability
Note: Content on OCM Solution's ocmsolution.com website is protected by copyright. Should you have any questions or comments regarding this OCM Solution page, please reach out to Ogbe Airiodion (Change Management Lead) or the OCM Solutions Team today. OCM Solution was previously known as Airiodion Global Services (AGS).
Images: Microsoft 365 Clip Art Image(s) (Bing images licensed under the Creative Commons license system.), https://pixabay.com/photos/application-request-ipad-tablet-1883453/, https://www.ls.graphics/free/free-pixel-4-and-pixelbook-go-mockup